Motivation

In the post-desktop era of computing, “people live, work, and play in a seamlessly interweaving computing environment”. A major goal of such Pervasive Computing scenarios is to support several parties with the appropriate technologies in order to facilitate a seamless cooperation and collaboration.
However, the involved parties may have mutual competing security requirements and goals, due to different organizational, legal and personal backgrounds.
We believe that it is a major research challenge to deal with this issue and to provide concepts and mechanisms for multilaterally secure pervasive cooperation.
In this research project, we deal with the following main research challenges:
- First of all, Pervasive Computing builds upon a close interweavement of the physical world and the digital world. What are the adequade security approaches and trust anchors that enable participation within Pervasive Computing environments?
- Since most information that is collected and processed by the pervasive infrastructure represents real world facts, data security vulnerabilities may become real world vulnerabilities. And while the availability of fine-grained records of user actions inherently causes privacy concerns, also, virtually any (non) action can potentially imply juridical or financial consequences. How can individual privacy protection, 3rd party accountability and law enforcement capabilities be reconciled in order to enhance the multilateral acceptability of pervasive ICT?
- On the other hand, once the individual wants to remain anonymous, it is difficult for an interested user to communicate with possible interaction and collaboration partners. What are the concepts that enable a user-friendly yet end-to-end secure pervasive communication?
Approach
In this project, we contribute a novel integrated approach to Multilaterally Secure Pervasive Cooperation as well as the supporting security techniques and mechanisms:
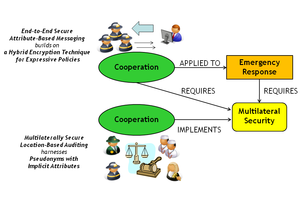
1) Pseudonyms with Implicit Attributes, an approach to multilevel linkable transaction pseudonyms, that is based on threshold encryption, secure multiparty computation and cryptographically secure pseudo-random number generators,

2) Multilaterally Secure Location-Based Auditing, a novel consideration of auditing mechanisms in the context of real-world actions, that reconciles privacy protection and accountability and proposes location traces as evidence,
3) Hybrid Encryption Technique for Expressive Policies, which allows encrypting under policies that include a continuous dynamic attribute, leveraging an efficient combination of ciphertext-policy attribute-based encryption, location-based encryption and symmetric encryption concepts. and

4) End-to-End Secure Attribute-Based Messaging, a communication mechanism for end-to-end confidential messaging with anonymous receivers that is suitable for resource constrained mobile devices; it also allows querying human sensors.
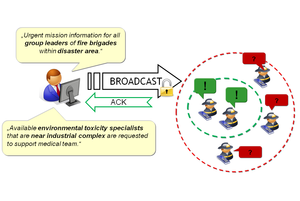
We motivate and evaluate our research results within challenging real world application scenarios. Hereby, one focus is given by mission-critical applications in the area of ICT-supported emergency response.
In this context, an efficient cooperation of multiple actors and parties is the key to successful incident responses – while demanding legally implied security requirements as well as individual privacy requirements have to be fulfilled. Our research draws from experiences with potential real users (German first responders and emergency decision makers).
Our proposed mechanisms for multilaterally secure data protection of location information are also part of the Simulation Study at CASED. The goal of the simulation of various legal court cases is to derive experiences with current and future technology in a realistic, safe environment, while both the technology and the regulations are still configurable.
Selected Publications
Weber, S. G., Multilaterally Secure Pervasive Cooperation, PhD thesis, Technische Universität Darmstadt, 2011 (online available / abstract)
Weber, S. G., Kalev, Y., Ries, S., Mühlhäuser, M., MundoMessage: Enabling Trustworthy Ubiquitous Emergency Communication, ACM International Conference on Ubiquitous Information Management and Communication (ICUIMC 2011), ACM Press, 2011 (online available)
Weber, S. G., Mühlhäuser, M., Multilaterally Secure Ubiquitous Auditing, Intelligent Networking and Collaborative Systems and Applications, Studies in Computational Intelligence, Vol. 329, Springer, 2010 (online available)
Weber, S. G., Martucci, L. A., Ries, S., Mühlhäuser, M., Towards Trustworthy Identity and Access Management for the Future Internet, The 4th International Workshop on Trustworthy Internet of People, Things & Services (Trustworthy IoPTS 2010), 2010 (online available)
Brucker, A. D., Petritsch, H., Weber, S. G., Attribute-Based Encryption with Break-Glass, Workshop in Information Security Theory and Practice, Springer, 2010 (online available)
Weber, S. G., Harnessing Pseudonyms with implicit Attributes for Privacy-Respecting Mission-Log Analysis, International Conference on Intelligent Networking and Collaborative Systems, IEEE CS, 2009. (online available)
Weber, S. G., Securing First Response Coordination With Dynamic Attribute-Based Encryption, Conference on Privacy, Security and Trust (PST 2009) in conjunction with World Congress on Privacy, Security, Trust and the Management of e-Business, IEEE CS, 2009. (online available)
Weber, S. G., Heinemann, A., Mühlhäuser, M., Towards an Architecture for Balancing Privacy and Traceability in Ubiquitous Computing Environments, Int'l Workshop on Privacy and Assurance, IEEE CS, 2008. (online available)
Weber, S. G., Ries, S., Heinemann, A., Inherent Tradeoffs in Ubiquitous Computing Services, GI Jahrestagung 2007, GI, 2007. (online available)
Please also consult the complete list of publications and do not hesistate to contact us, if you are interested in our research!
People
Scientific Advisor
- Prof. Dr. Max Mühlhäuser
Former Project Member
- Dr. Stefan G. Weber
- Dr. Sebastian Ries



